Arctic Wolf Labs has identified the rapidly growing Akira ransomware gang. Just revealed that the new group has ties to members of Conti, the former cybercrime superpower that shattered in 2022.
Akira has many characteristics that are now familiar territory for security researchers. The underlying business model is based on Ransomware-as-a-Service (RaaS), where the targets are not chosen directly by the creators of the software. Akira’s behaviour is quite opportune, according to Arctic Wolf, but it has struck home with at least 63 organizations.
Despite Akira’s concealment tactics, Arctic Wolf discovered that the gang shares similarities with the dreaded Conti collective, which was a highly successful group between 2020 and 2022. Conti was known for dealing with victims in a highly aggressive manner, evidently being cavalier about its own reputation. Immediately after Russia invaded Ukraine, Conti announced in February 2022 that it wanted to concentrate its efforts on aiding the Russian state. Shortly thereafter, the group fell apart due to internal disagreements: partly, these conflicts were based on the differing political beliefs among its members, but there were also complaints about the unequal distribution of proceeds from ransomware payments.
Methods
Akira was first detected in March of this year. Unlike Conti, the group does not target very large companies, but predominantly SMBs (small to medium-sized businesses). 80 percent of the victims are organizations with fewer than 1,000 employees. Akira seems opportune in its choice of targets: it encrypts files and exfiltrates data for subsequent study, then chooses the amount of the ransom. Again, this differs from the mostly targeted targets that Conti had. Equally different tactics than the premeditated attacks of a party like LockBit, which is the most prominent ransomware player this year.
Tip: LockBit 3.0, the market leader in ransomware
The amounts claimed are between $200,000 and $4 million, Arctic Wolf Incident Response insights show. Combined with a leak site, it pressures organizations to hand over ransom. Interestingly, there are choices available to the victim. For example, the gang can still negotiate the price for the “services rendered”: just a decryptor key will be cheaper than if they want to prevent the data from being out in the open.
Arctic Wolf found that the victims almost always had compromised login credentials. In addition, the majority of these organizations did not have multi-factor authentication (MFA) set up on their VPN services. It is possible that the attackers obtained the data through a darkweb trading site. Consider a player like Genesis Market, which was shut down by authorities earlier this year.
Tip: Dutch ringleader of Genesis Market arrested
Similarities with Conti
In many ways, Akira is not at all reminiscent of the Conti group. However, Arctic Wolf discovered that there actually is a significant overlap with the split-up gang. First of all, there is a similarity when it comes to the programming code Akira uses. For example, it ignores the same file types as Conti and likewise uses the ChaCha algorithm to encrypt files. Since June 29, however, Avast has released a decryptor for Akira, forcing the gang to opt for another method of encryption after this date.
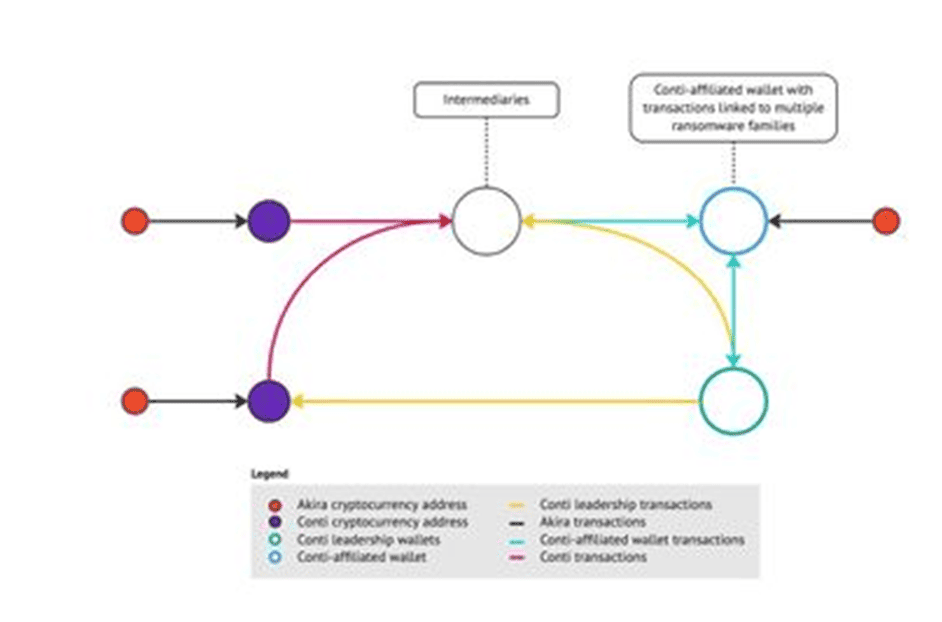
The “smoking gun” for the ties with Conti is found in the blockchain analysis conducted by Arctic Wolf. Despite cryptocurrencies being challenging to track, they have to be recorded in a blockchain ledger. This is the only way to keep track of transactions worldwide. The researchers found out that some of the payments were made through a well-known Conti crypto wallet, thus proving that some of Conti’s infrastructure survives in the new criminal venture.
The future
Akira’s example indicates that breaking up one ransomware gang does not immediately lead to the creation of an equally large successor. Conti’s breakup previously led to the continued growth of Karakurt, which also has ties to the Diavol ransomware gang. In particular, this group is said to target organizations that have already been attacked before.
We might expect that taking out a ransomware group would have results. However, it is also true that threat actors in not-too-friendly countries are almost impossible to eliminate completely. Russian hackers may heed Conti’s call and attack Western organisations on their own country’s behalf. Still, Akira proves that behavioural change is possible. Akira’s expediency and less aggressive tone indicates that the nature of the threat can change fundamentally with changes in the cybercrime landscape.
Akira is no direct successor to Conti, but its rapid growth is an indication for how quickly the field of play shifts in the online crime world.
Also read: Meet NoEscape, the return of the Avaddon RaaS gang