Chinese hacker group Storm-0558’s attack on Microsoft in 2023 should never have happened. That is the conclusion of the U.S. Cyber Safety Review Board (CSRB). In the report, the CSRB describes a host of security flaws that made the infiltration possible.
Microsoft, aside from being active in a wide range of sectors, is the world’s largest security vendor. Its annual revenue from offering security products has reached beyond $20 billion. Nevertheless, hackers from both Russia and China managed to gain far-reaching access to Microsoft systems over the past 12 months. While the CSRB report is limited to the Chinese incident, we previously covered the Russian Midnight Blizzard/Nobelium attack in detail. You can read more about that in our separate article.
State Department saw the first signs
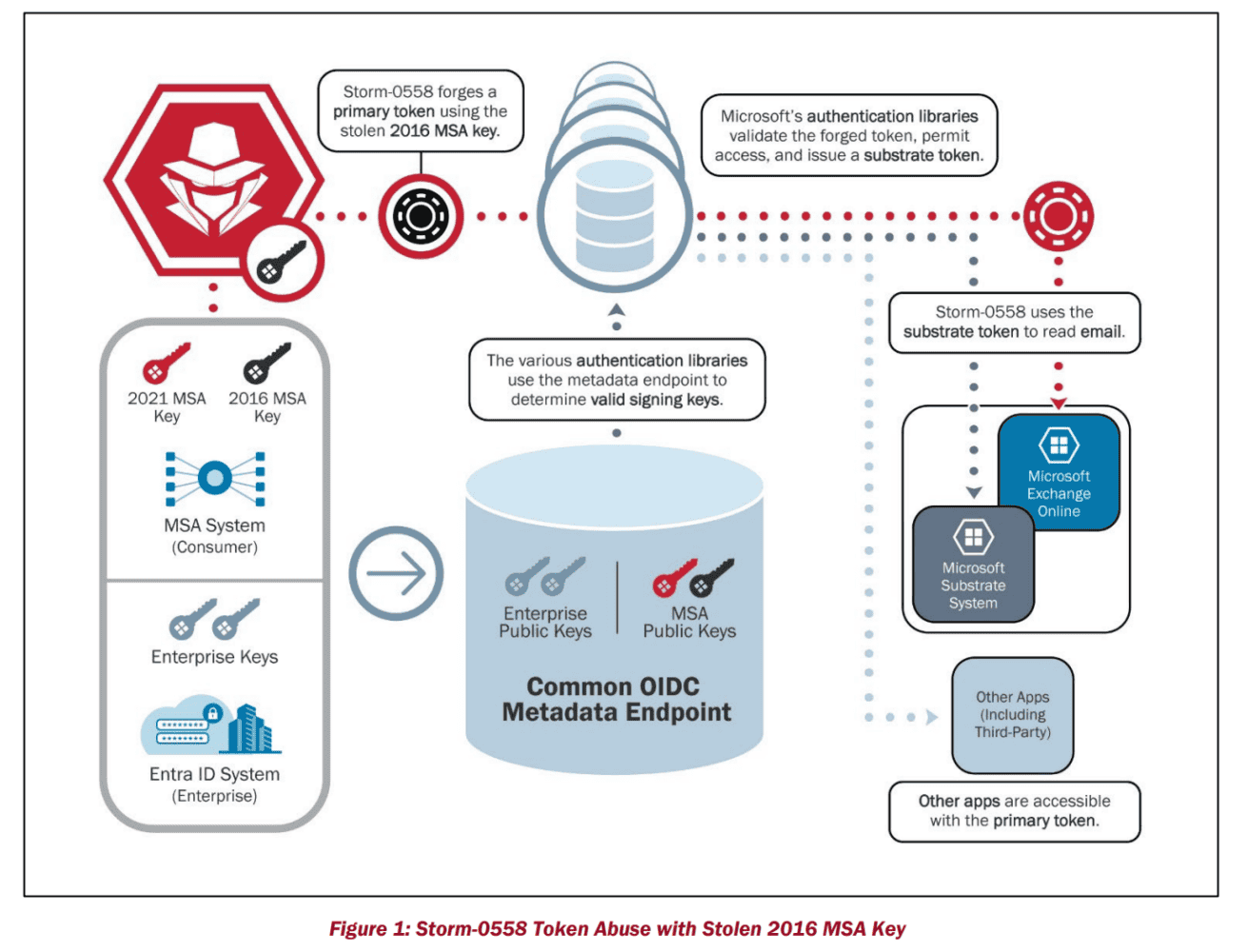
The U.S. State Department detected the first traces of the Chinese attack. Ultimately, the hackers were found to have hit 22 organizations, including many government agencies. By obtaining a 2016 Microsoft key, the Chinese attackers were able to get inside the mailbox of U.S. and European policymakers for up to six weeks. In the U.S., the hack affected Commerce Secretary Gina Raimondo and China Ambassador R. Nicholas Burns, among others. Thanks to the paid Microsoft Purview Audit (Premium), U.S. authorities had access to detailed data logs of the incident. Without the exclusive MailItemsAccessed log, security teams couldn’t have figured out what the hackers had done.
Microsoft was notified shortly after the discovery on June 16, 2023. Within the next ten days, the actual scale of the Chinese operation became evident. Outside parties also gained insight into the matter. In late July, security company Wiz already revealed that the infiltration was more widespread than previously thought. The attack vector was clear, too. A zero-day vulnerability in GetAccessTokenForResourceAPI led to the exposure of all Azure Active Directory applications (now Entra ID). However, all the compromised data was located on the Microsoft Outlook web application (OWA).
Tip: Hackers obtained mass access to user accounts with Microsoft key
Microsoft does not convince with explanation
It’s still not known how Storm-0558 obtained the Microsoft key that was created in 2016. The leading theory over at Microsoft is that the attackers exploited a “crash dump,” in which system memory is readable in a frozen state, usually when an application has crashed. Microsoft claims that stealing these keys is no longer possible via this method. However, according to the CSRB, the company still has not proven this is even how the Chinese hackers got the key. In addition, Microsoft links an earlier incident related to Storm-0558 from 2021 to the infiltration last year. For that connection, as it happens, the evidence also isn’t sufficient, at least according to the CSRB.
A major shortcoming of Microsoft’s key distribution was that the appropriate teams could not automatically see how old an active key was. This resulted in the ability for Chinese hackers to generate fake authentication tokens with their stolen key.
On top of that, cloud providers (CSPs) fail to always log or disclose vulnerabilities publicly. “This lack of disclosure, which is counter to accepted norms for cybersecurity more generally, makes it difficult for CSP customers to understand the risks posed by their reliance on potentially vulnerable cloud infrastructure,” the CSRB noted.
Much known about attacker, but too little protection
State actor Storm-0558 is persistent. Since 2000, the group has set up large-scale espionage operations against the West and other parties unfavourable to China, such as Taiwan and the Uighurs. Previously, the hackers were allegedly responsible for global campaigns against Google, Adobe and RSA. The high quality of their tooling and methods of information collection show that Storm-0558 is extremely sophisticated, the CSRB states.
The CSRB emphasizes that cloud providers today hold highly sensitive data and therefore bear great responsibility. Despite the major errors that it found when researching the Chinese incident, the government body states that Microsoft was cooperative in the investigation and acted to the best of its ability.
Still, a critical note can be added. When Microsoft hadn’t yet collected all the details of the attack, it waited to contact government body CISA until it did so. This approach is understandable, as a company should generally prefer to present a complete and clear picture to outside parties as soon as they establish contact. However, Microsoft’s public blogs incorrectly described Storm-0558’s tactics on several occasions. It shows that earlier warnings to outsiders, even when the information is incomplete or turns out to be incorrect later, should be preferred.
‘Inadequate security culture’
All of this points to an “inadequate security culture” within Microsoft, the report concludes. The company regularly ignored known best practices, mostly chose performance and uptime over security, and did not subsequently correct significant errors in published blogs. Only at the urging of the CSRB did Microsoft correct its descriptions of important details.
The CSRB cited a 2002 quote from then Microsoft CEO Bill Gates, in which he emphasized the importance of security over new features and the prevention of downtime. According to the CSRB, the Redmond tech giant has since drifted away from this ethos. Therefore, current CEO Satya Nadella and the rest of the company’s C-suite should now focus on these fundamental security concerns. Both literally and in spirit, the report is repeating the lessons Bill Gates tried to convey to his staff more than 20 years ago. Now that Microsoft is the world’s largest security player, those lessons are more important than ever.
On top of that, the report argues that cloud vendors should provide logging capabilities to customers for free whenever possible so that detection can occur as quickly and in as much detail as possible. After all, a smaller cloud customer would never have been able to detect a large-scale spying operation of this nature had taking place. The only hope is that the likes of Storm-0558 will always target more valuable assets. However, that’s no way to offer security.
Also read: China blocks Windows, Intel and AMD for government use