In addition to improving its infrastructure offerings, Hashicorp is also updating the other part of its product portfolio: security lifecycle management. Additions include dynamic, unique secrets for short-term access to critical systems and autorotation of credentials. Both features are part of the Vault Secrets offering. Vault Radar and Boundary have also been improved.
Vault is the tool within the HashiCorp portfolio for managing secrets, such as API and encryption keys, passwords, and certificates. It consists of Secrets and Radar, with the former providing far-reaching automation of secret management and the latter actively searching for unmanaged credentials. Both have been expanded: for example, Radar now integrates the ability to proactively block the accidental exposure of secrets to the outside world.
The feature is a direct response to a weakness in some Git workflows that causes servers to log code while secrets may still be present in it. The pre-receive scanning functionality in Vault executes a script for detecting such secrets and, upon detection, blocks and reports them to whoever needs to mitigate the issue before the secrets can end up in the code repository.
Agents patrolling for sensitive data
Another addition to Vault radar is the Agent functionality. This is intended for users who, due to company policy or legislation, prefer to keep their code, tools and data in a private environment. Because workloads occasionally have to go to cloud environments, HCP Vault Radar’s agent helps these organizations keep the sensitive information associated with such workloads safely in their private systems.
At the same time, it enables clients to send said workloads or processes to the cloud without any problems. Thus, the agent here acts as a kind of border guard, stopping specific data but letting safe data pass without causing problems for the workload that needs to run in the cloud environment.
Both pre-receive scanning and the agent functionality are now available for free in public beta. For users needing problem-solving in this department, HashiCorp offers a variety of remediation best practices, such as for active and inactive secrets and secrets leaked from Google or AWS cloud environments. In doing so, HashiCorp’s SecOps team can help set up configurations that fit the customer’s specific policies.
Autorotation and dynamic secrets
Vault Secrets gains several important features, i.e. autorotation of secrets and dynamic secrets. The former is now generally available; the latter is in public beta. The autorotation of sensitive data such as keys and passwords removes the need to manually manage and regularly refresh all kinds of static secrets, as this is now done automatically. This simplifies the management of such secrets, makes the systems and processes to which the secrets give access much less susceptible to leaks, and simplifies compliance.
Vault Secrets auto-rotation is currently only available for AWS IAM user access keys, Google Cloud service account keys, MongoDB usernames and passwords, and Twilio API keys. It will eventually also become available for private databases.
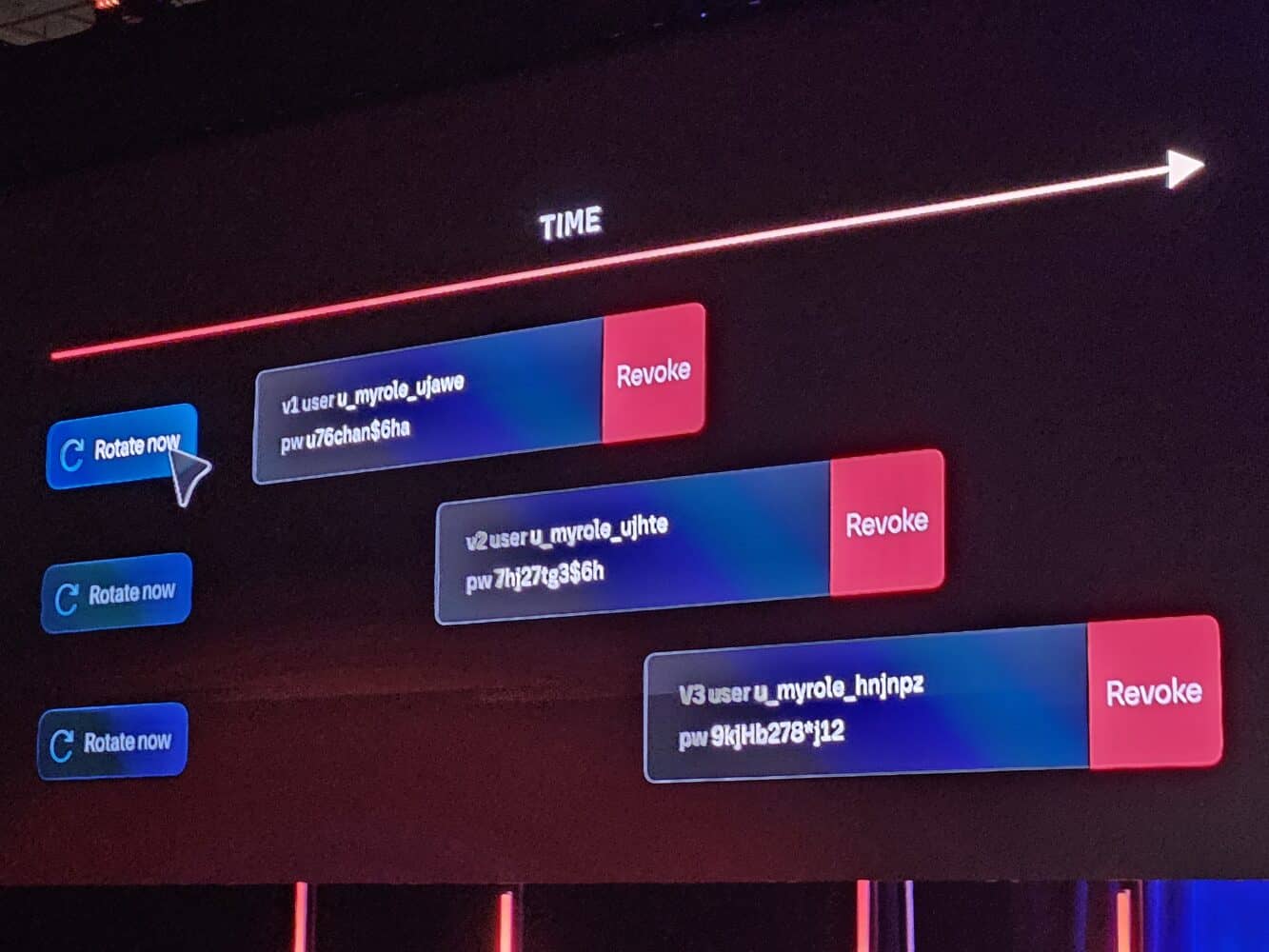
Dynamic secrets allow Vault to generate short-term, unique credentials for individual users. These credentials may last only a few minutes. This option is available for Google Cloud, AWS, and HashiCorp’s own HCP Terraform. Dynamic credentials for provisioning via Terraform are another addition to the Vault Secrets offering.
Vault Secrets provides the temporary credentials for such provisioning on a cloud vendor’s environment, eliminating the need for static passwords and keeping the environment open no longer than necessary for provisioning. Also, through the general log functionalities in the HashiCorp Cloud Platform, this service keeps track of which short-term secrets have been generated.
Thousands of credentials lying around
The emphasis on shortening the lifespan of credentials and, if possible, providing unique ones, is one of those topics that HashiCorp repeatedly comes back to. According to the company, it is an open secret that many organizations, including—or perhaps especially—very large ones, have thousands of secrets lying around, many of which unmanaged. From sensitive data in Slack channels to Excel sheets containing all the passwords for a user or department, there is no scenario HashiCorp’s staff hasn’t encountered in the wild.
By offering a suite of products that can dramatically reduce that attack surface and simplify its management, the company believes it can deliver an important value proposition to the enterprise organisations it would like to have or keep as customers.
Audit log streaming for Vault, Boundary and Packer
New features from the enterprise version of Vault that have found their way into the HCP version involve increased control over access management. This can now be controlled not only for an organisation or project but also at the level of individual applications and persons. Also, Vault, Boundary (about which more below), and Packer now have audit log streaming available in public beta. This feature enables access requests to secrets to be precisely tracked, improving observability. Records are retained if needed for audits.
Boundary controls human users’ access to sensitive systems. According to the company, overprovisioning users is a regular occurrence, which results in them getting far more access than they need to perform their jobs. Boundary delineates where access is necessary per user, department or role and, more importantly, where it is not. Again, the strength here is that this is automated as much as possible, and administrators have little to worry about after initially setting the parameters.
Transparent sessions
When human eyes and hands do need to be involved, a log of everything is available. The novelty here concerns transparent sessions, allowing authorized users remote access to sensitive systems without them noticing any login or verification process. That all happens behind the scenes and doesn’t bother users. The magic behind this is that Boundary intercepts DNS calls and routes them to the right system.
To conclude the series of announcements and improvements, it’s worth noting that the version of Consul for Kubernetes now comes with DNS views. Where Boundary controls access from people to systems, Consul controls communication and access between systems. The new DNS views feature gives more insight into multi-tenant environments and allows administrators to shield these tenants from each other where necessary or, conversely, facilitate queries from services that reside in the same partition.
Also read: HashiCorp brings stacks to Terraform and doubles down on scalability
