An advanced phishing campaign attacked hundreds of companies’ Microsoft Azure accounts. Once the hackers got the login information, the accounts were hijacked with various forms of MFA.
According to Proofpoint security researchers, hundreds of Microsoft Azure accounts within companies have recently been attacked by an advanced phishing campaign. The campaign mainly focuses on stealing sensitive and financial data. In addition, the hackers want to compromise mailboxes. It is not known which hackers are behind the attacks.
All employees within companies with a Microsoft Azure account are targeted. The most targeted victims hold the roles of sales director, account manager and finance manager. C-level management is also heavily targeted. By targeting all levels, the hackers want to gain the widest possible access to corporate Azure accounts, is the thinking.
Attack plan and MFA encryption
The phishing campaign starts by sending emails to account holders. Individual phishing is hereby combined with shared documents. These shared documents have links that redirect users to a phishing web page. Hackers obtain login credentials through this page, and with this information, they can pass on to hijack accounts.
Once the hackers have taken over an account, they secure this access with various forms of multifactor authentication (MFA). This makes it more complex to recover the affected accounts with new passwords or check recent logins.
MFA methods used include temporary passwords via email or phone numbers. They usually use an authenticator app.
Hard to catch
In addition, the researchers found that the breaches came from various proxies. These proxies are a kind of intermediary between the infrastructure used by the hackers and the attacked accounts.
The proxies help align the geographic location of the connecting IP address with the region in which the victims are located. This allows geographical restrictions to be bypassed. The proxies also change regularly, making it more difficult to combat the attacks and block malicious IP addresses.
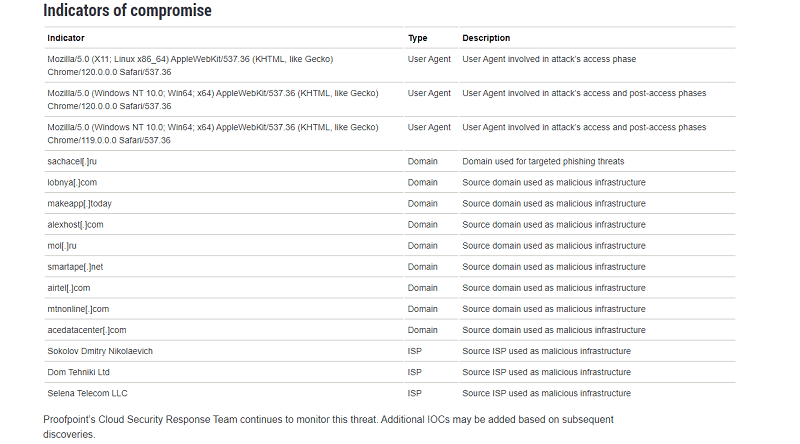
List of indicators
Azure users can check if they are a target. The best indicator, according to the researchers, is a dedicated Linux user agent, such as Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, as Gecko) Chrome/120.0.0.0 Safari/537.36.
Proofpoint has additionally published a list of more possible indicators. The security specialists want users to keep a close eye on these indicators.
Also read: Microsoft most spoofed brand for phishing attacks