The process injection vulnerability allows access to webcams, microphones and sensitive information.
Thijs Alkemade, an ethical hacker from Computest Security, discovered a way to circumvent security measures within Apple’s operating system. It bears some resemblance to Alkemede’s discovery in the summer of 2022. That discovery, too, involved a process injection vulnerability in macOS that allowed malicious actors to gain access to the system.
The vulnerabilities bypass the operating system’s security measures. Normally, an application on a Mac cannot simply access sensitive data. For this, the user must first give permission. Think of permissions to access the webcam or documents. However, the vulnerabilities made it possible to completely bypass this permission, potentially leading to access to all data.
Command execution
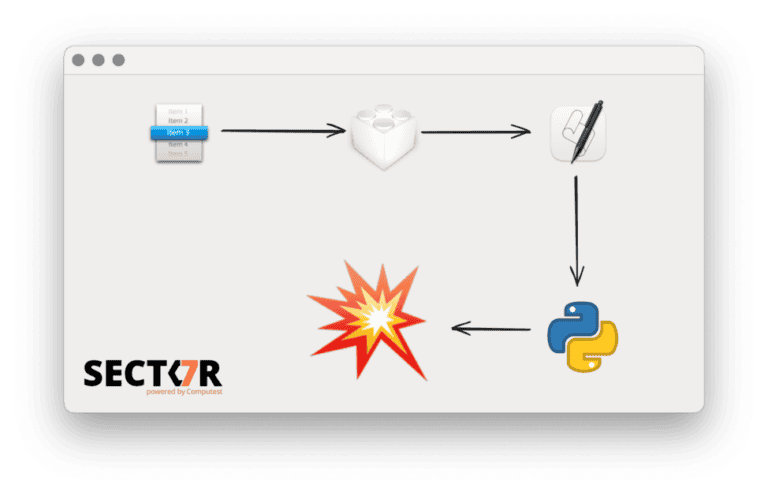
In an extensive blog, Computest discusses how the new process injection vulnerability works. Alkemade discovered that executing shell commands leads to obtaining the application’s TCC permissions. With each command the ethical hacker executed, he could gain access to the microphone and webcam, provided the original application already had permission. He was also able to access the user’s geolocation and sensitive files from the Mail.app database.
Computest did add, “We did not find a way to escape the sandbox, as sandboxed applications can not copy another application and launch it. While nib files are also used in iOS apps, we did not find a way to apply this technique there, as the iOS app sandbox makes modifying another application’s bundle impossible too. Aside from that, the exploit would also need to follow a completely different path, as bindings, AppleScript and Python do not exist on iOS.”
The vulnerability is now no longer present in the operating system. However, it took some time for Apple to fix the vulnerability because it was a design flaw. An initial fix appeared in October 2022 with macOS 13.0, but it proved easy to bypass. The release of macOS 14.0 in September 2023 did bring the correct fix. Now that the fix is in place, Alkemade can go public with the details.