Security researchers warn of the particularly dangerous Muddling Meerkat, which bypasses traditional security measures for potentially disruptive attacks against critical infrastructure.
A research report shared with us by discoverer Infoblox Threat Intel discusses the new threat in detail. Based on data, security experts state that, in all likelihood, Chinese hackers are behind Muddling Meerkat. In particular, the role of Muddling Meerkat in disrupting China’s Great Firewall (GFW), which prevents citizens from accessing websites and services labelled as illegal, is attracting attention.
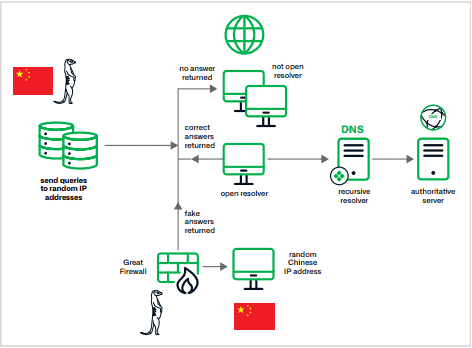
The attacks look like a DDoS attempt, but Infoblox says they probably involve a different purpose. In the image below, Infoblox shows a simplified visual representation of Muddling Meerkat’s modus operandi, noting that the modus operandi is complex in itself. So we discuss more about how it works below the image.
DNS and MX queries
Infoblox was able to draw some concrete conclusions about Muddling Meerkat based on the data. For example, the data shows that servers with Chinese IP addresses were used to run campaigns. These execute DNS queries for random subdomains of IP addresses globally to probe IP addresses globally.
In addition, they use MX (Mail Exchange) record queries in combination with other record types. This results in short random hostnames of a set of domains outside the attacker’s control in the .com and .org top-level domains (TLDs). On the other hand, they cause fake MX records of Chinese IP addresses injected by the GFW.
Muddling Meerkat also uses “super-aged” domains, or domains often registered before the year 2000. That way, it avoids DNS block lists and prevents clashing with Active Directory domains. When choosing domains for abuse, it favors length in addition to existence time rather than current status and ownership. Many domains are abandoned or reused for questionable purposes, while others are used by legitimate entities.
Other features of Muddling Meerkat are:
- They run campaigns of one to three days continuous.
- They probably do not use IP address spoofing on a large scale but initiate DNS queries from dedicated servers.
- They are limited in size to avoid detection.
- There may be execution in separate components, leading to different DNS patterns.
- It began on or about Oct. 15, 2019.
Tip: Despite export bans, China has gained access to new AI chips