Docker Hub repositories have been massively used to spread malware and phishing websites since 2021.
Docker Hub, Docker’s service that allows developers to find and share container images, is being abused by cybercriminals. That’s the finding of research by JFrog. About 20 per cent of the 15 million Docker Hub repositories are being abused for this purpose. The malware found ranged from spam to phishing websites.
The researchers uncovered about 4.6 million Docker repositories that did not contain Docker container images. These repositories could not be used with a Kubernetes cluster or a Docker engine.
In addition, JFrog researchers discovered that three major campaigns were active, using 2.81 million of the suspected Docker Hub repositories found for malicious purposes.
Different malicious methods
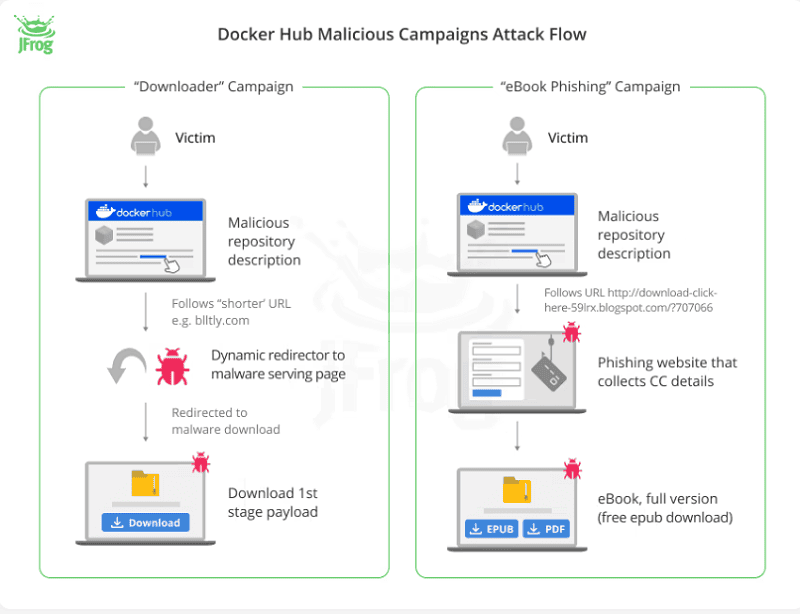
These malicious campaigns used different methods to create and distribute the repositories. The so-called ‘Downloader’ and the ‘eBook-phishing’ campaigns used fake repositories in batches. The ‘Website SEO’ campaign created several repositories daily for its malicious activities and had a single user per repository.
Target campaigns
As malicious activity, the Downloader campaign used automatic text generation with SEO to recommend pirated content and cheats for games and software links. This campaign occurred in 2021 and 2023. JFrog researchers believe this campaign is part of a larger malware campaign that installs adware and third-party software.
The eBook Phishing campaign focused on creating about a million repositories to offer free ebook downloads with descriptions and download URLs. Although a free ebook was promised, users still must enter credit card information.
According to the researchers, the purpose of the Website SEO campaign is unclear. Most of the content distributed in the repositories is harmless, and all have the name website. JFrog believes this campaign was a possible stress test before launching malicious campaigns.
Docker has since removed all malicious repositories found from Docker Hub.
Also read: Cisco firewalls exploited by state-sponsored hackers