Hackers have found yet another way to get the well-known Malware-as-a-Service (MaaS) Lumma Stealer into the devices of unsuspecting and unwilling internet users. This time it involves infected CAPTCHA verification pages. Clicking the familiar ‘I’m not a robot’ button eventually leads to the download of a malicious payload.
This relatively recent malware campaign has been discovered by cybersecurity firm Qualys’ Threat Research Unit (TRU). It involves phishing sites hosted by various providers, often through Content Delivery Networks (CDNs). One such CDN involves one from Cloudflare. Victims think they are downloading legitimate software that requires them to perform verification via CAPTCHA. Once they do so, they are instructed to open the Microsoft Management Console via Windows+R. Then, they must paste a piece of code secretly copied to the clipboard and click ‘OK’.
A PowerShell command is then executed through some hidden steps. This eventually leads to searching for sensitive information on the user’s device and exfiltrating it. Experienced computer users may wonder why a CAPTCHA would ask them to paste and execute code through the console. Still, for companies with many employees who may not all be equally computer-savvy, this method of installing malware does pose a risk.
Multiple payloads
The attack chain uses a multi-stage fileless approach, making detecting it more difficult. It uses mshta.exe, a legitimate Windows utility that executes embedded scripts in HTML applications, to download and execute malicious payloads in this case. The malware retrieves encrypted JavaScript code that eventually downloads the Lumma payload via a second PowerShell script. This script downloads additional payloads in the form of “K1.zip” and “K2.zip,” “VectirFree.exe” and DLLs from Lumma Stealer. VectirFree.exe nestles into the legitimate software BitLockerToGo.exe to hide malicious code, i.e. process hollowing.
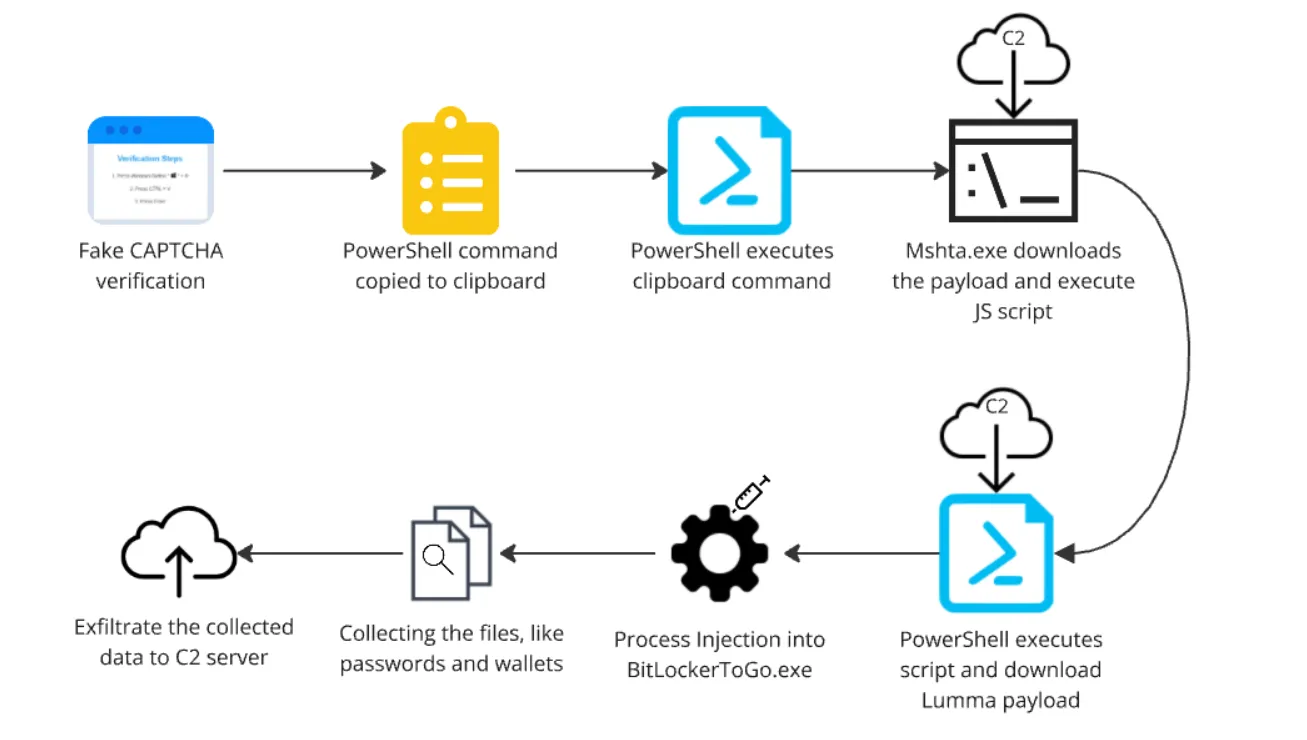
Once installed, Lumma Stealer actively searches the affected system for sensitive data, targeting files related to cryptocurrency wallets and password management. For example, the malware looks for keywords such as seed.txt, pass.txt, *.kbdx, ledger.txt, trezor.txt, metamask.txt, bitcoin.txt and wallet.txt.
After collecting the data, Lumma Stealer communicates with Command and Control servers, which use domains with the “.shop” top-level domain (TLD) for exfiltration. Although the servers under investigation are currently off the air, that doesn’t mean they will stay that way. Not surprisingly, then, Qualys recommends its own Endpoint Detection and response (EDR) solutions to detect threats like these or, preferably, cut them off altogether by interrupting the malicious scripts.
Also read: AI image model manages to crack CAPTCHAs
