Apple will encourage and reward ethical hackers for finding bugs in its Private Cloud Compute (PCC) system for handling complex AI processes. To do so, the tech giant is making available a special virtual research environment and making certain AI system code open-source.
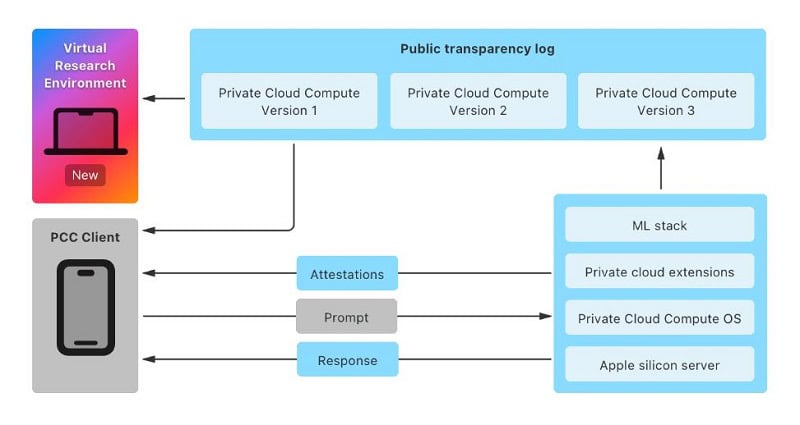
Apple wants to improve the security of its PCC by allowing developers to research the security of this environment. PCC is Apple’s cloud-based intelligence system for processing complex AI processes with end-user data, subject to high privacy standards.
PCC processes end-user personal data in a way that does not compromise its privacy or use it in any way other than strictly necessary. This is done using end-to-end encryption.
This encryption guarantees that Apple employees cannot access this data and that the system resists hacking attempts. All privacy and security measures are also completely transparent to users.
Introducing virtual research environment
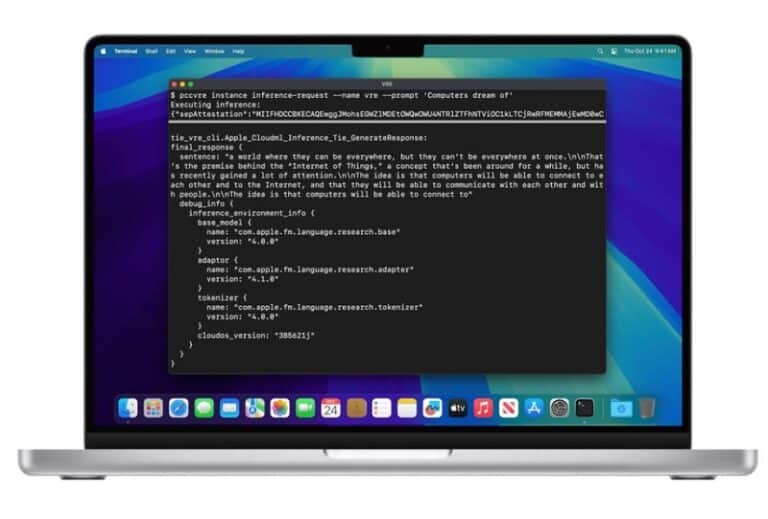
To further enhance PCC’s privacy and security standards, Apple is now making a virtual research environment (VRE) available to developers to identify vulnerabilities. To this end, the tech giant has also open-sourced the source code of some key components and published a Private Cloud Compute Security Guide explaining PCC’s architecture and technical operation.
The VRE allows developers to replicate and examine a version of PCC locally, testing its privacy and security functionalities and looking for potential vulnerabilities.
Reward bugs via bounty program
To detect vulnerabilities in PCC, Apple is introducing new capabilities within its existing security bounty program, which rewards discovered vulnerabilities in Apple products and software.
The highest reward for vulnerabilities in PCC is $1 million for a successful attack that accesses data and enables RCE (Remote Code Execution). Investigators who gain access to end-user request data or other sensitive information receive $250,000. Attacks from networks with elevated privileges are rewarded between $50,000 and $150,000.
Rewards are also available for vulnerabilities that fall outside these categories.
PCC’s VRE is now available within macOS Sequoia 15.1 Developer Preview. Researchers need a Mac computer with an Apple processor and at least 16 GB of unified memory to run this environment.
Also read: Is Apple replacing its fixed release cycle?