Increasingly, cyber threats are being spread via encrypted data traffic. As many as 87 percent of all cyber threats today are spread via encrypted data traffic, up 10 percent from 2023.
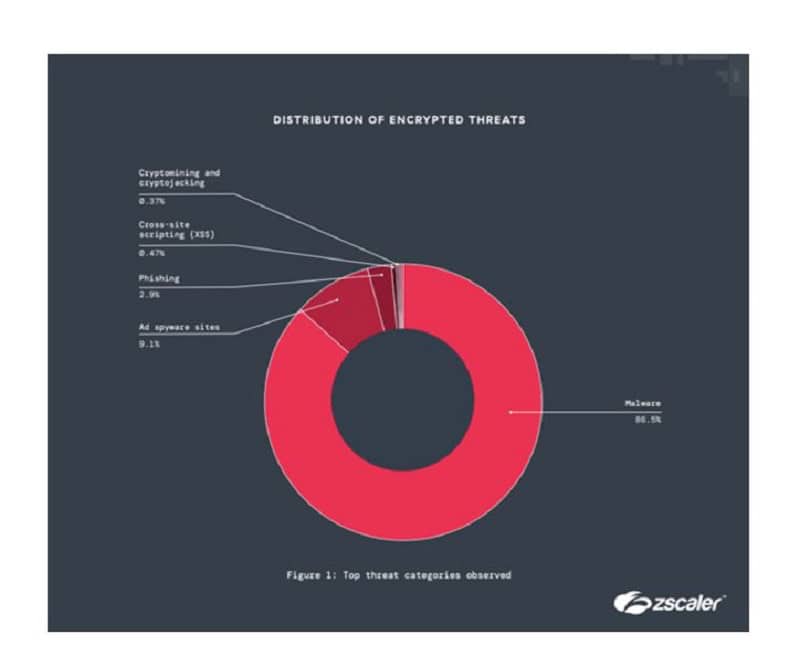
That’s according to the recent Zscaler ThreatLab 2024 Encrypted Attacks Report. Encrypted data traffic is supposed to prevent breaches, but it still appears to harbor many cyber threats. 90 percent of the cases involve malware, phishing threats, and cryptominers. The percentage of malware distributed, 86 percent of all threats, was up 19 percent from last year. In particular, this included spreading malicious web content, malware payloads and macro-based malware.
The researchers indicate that hackers’ growth of distributed malware is a clear strategic change. As a result, they want to focus their attacks more on encrypted traffic.
Cryptomining/cryptojacking attacks via encrypted data traffic increased by 123 percent, those for cross-site scripting by 110 percent and those for phishing by 34 percent.
Other notable results from the survey include that the manufacturing sector was the most affected by attacks conducted via encrypted data traffic. Other vulnerable industries include the ICT sector, services, education and retail and wholesale sectors.
The most attacks using this attack vector occurred in the United States, India, France, the United Kingdom, and Australia.
Clear attack path
The researchers also indicate how an attack via encrypted traffic often proceeds. First, hackers explore how best to attack a target’s network. Then, often through exploits, brute force attacks or stolen login credentials, they break into the network in question. Once inside, they perform lateral moves, escalate privileges, and provide persistence.
In the final phase, they execute their targets, often stealing the data to monetize this valuable information later through extortion or other attacks.
Possible protection options
According to Zscaler researchers, companies can best protect themselves from attacks via encrypted data traffic by taking several measures.
First, they must realize that any Internet-connected device or service is vulnerable to attack. In addition, it is important to inspect all incoming encrypted data traffic for threats and – if possible – block them.
In particular, it is helpful to use a zero trust architecture to holistically protect all connections between end users and applications, with IoT and OT systems, locations and branch offices, and also among themselves between cloud-based workloads.
Furthermore, microsegmentation is important for restricting access to systems and applications, including to authorized end users. Using an AI-supported cloud-based sandbox environment can also help. This provides isolation and quarantine of unknown attack attempts to prevent “patient-zero” infections.
In addition, Zscaler indicates that companies can limit the number of environment entry points. They should also inspect outbound northbound and southbound data traffic to prevent Command and Control (C2) traffic and protect sensitive data.
Also read: Zscaler brings zero trust segmentation to offices and factories
