The Trend Zero Day Initiative (ZDI) has found 11 hacker groups with state support from North Korea, Iran, Russia and China exploiting a previously unknown Windows vulnerability. The attacks focus on spying and data theft via shortcut files, but Microsoft refuses to fix the underlying problem.
Trend Micro’s ZDI team has identified nearly a thousand malicious Shell Link (.lnk) files that exploit vulnerability ZDI-CAN-25373. The actual number of attacks is likely much higher. Despite a submitted proof-of-concept to Microsoft, the latter has decided not to release a security patch.
Speaking to The Register, a Trend Micro researcher stated that the technical fix may be “incredibly difficult” to implement for Microsoft. The tech giant itself told the same news organization that the threshold for direct intervention had not been reached with the investigation, although it was appreciated.
North Korea leader in vulnerability abuse
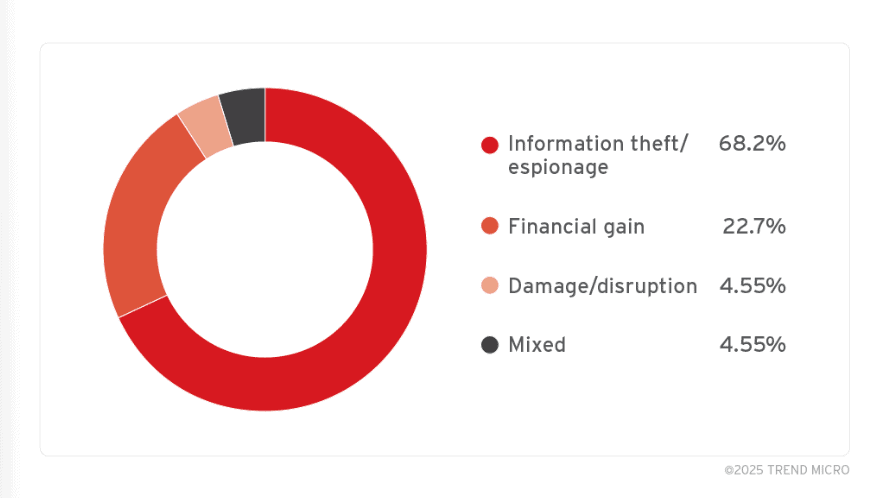
Nearly half of the state-sponsored attackers abusing the vulnerability are from North Korea. This indicates a trend of cooperation and sharing of techniques between different hacker groups within the North Korean cyber program, according to the ZDI team. The analysis shows that about 70 percent of the attacks are aimed at espionage and information theft, while more than 20 percent are financially motivated.
The vulnerability affects the way Windows displays the contents of shortcut (.lnk) files. Attackers can prepare a malicious .lnk file that looks perfectly legitimate to users, while containing malicious code.
Industries affected and geographic distribution
According to the survey, attacks primarily target government agencies, financial institutions (including crypto companies, regular targets of cyber attacks as the one on ByBit recently revealed), think tanks, the telecom sector and defense. Most attacks were detected in North America, but the researchers see a global impact extending to Europe, Asia, South America, Africa and Australia.
The researchers were also able to identify several malware payloads distributed through this attack vector. Interestingly, the cybercriminal group Water Asena (Evil Corp) used the vulnerability in their Raspberry Robin campaigns. This collective was described by Microsoft in 2022 as a prominent “pre-ransomware” group, speculating on a payment model for the number of times malware was successfully installed.
Organizations in the aforementioned high-risk sectors are strongly advised to scan their systems for possible compromise and remain vigilant about .lnk files in general. The zero-day vulnerability remains an active threat as Microsoft has not released a patch.