Tens of thousands of repositories have fallen victim to a supply chain attack via a GitHub Action. Security specialists at Wiz discovered a link to the earlier GitHub Action attack.
Last week, security specialists at StepSecurity found an attack on approximately 23,000 GitHub repositories via GitHub Actions. The attack exploited the popular “tj-actions/changed-files” workflow, allowing cybercriminals to inject malicious code and gain access to CI/CD secrets. This made it possible to steal data.
The attack was carried out using a compromised GitHub Personal Access Token (PAT), used by a bot (@tj-actions-bot) with extended access privileges. How this token was captured was initially unclear.
Cause in previous supply chain attack
Security specialists at Wiz claim that the source of the compromised PAT lies in a series of previous supply chain attacks. This series began with an attack on the GitHub Action ‘reviewdog/action-setup’ from the Reviewdog working group.
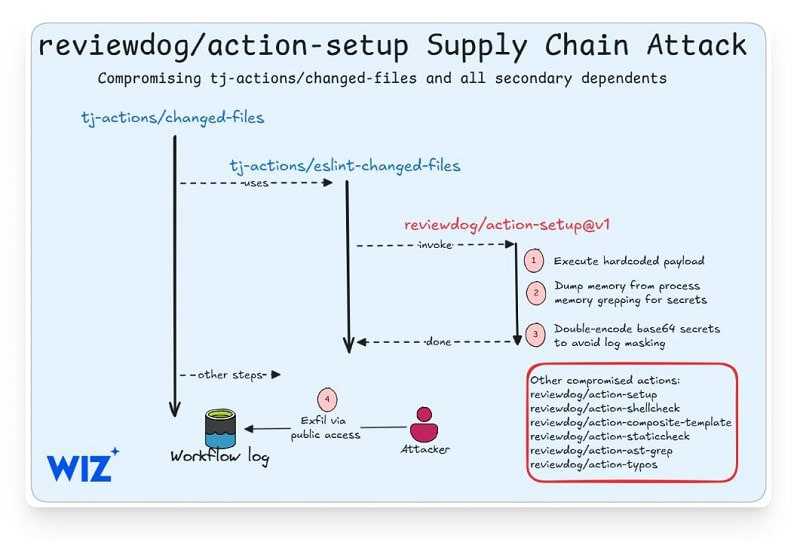
Hackers compromised the v1 tag of this action and added base64-encoded code, dumping CI/CD secrets into log files. Because these log files are publicly accessible, the attackers could easily capture secret data.
The GitHub Action ‘tj-actions/eslint-changed-files’ uses ‘reviewdog/action-setup’, which allowed the stolen PAT to be captured via a log file. This makes ‘reviewdog/action-setup’ the original cause of the recent GitHub Action leak.
Other GitHub Actions are also at risk, including: reviewdog/action-shellcheck, reviewdog/action-composite-template, reviewdog/action-staticcheck, reviewdog/action-ast-grep and reviewdog/action-typos.
Reviewdog workgroup is very vulnerable
The vulnerability within Reviewdog has been fixed by accident. Still, researchers warn that the Reviewdog workgroup remains vulnerable, especially since it automatically accepts new members, increasing the risk of future attacks.
Recommendations
Wiz advises developers to check their repositories for the presence of “reviewdog/action-setup@v1”. If double-encoded base64 payloads are found in the workflow logs, this indicates a data breach. Developers should then immediately remove all references to affected actions, clean up logs and refresh exposed secrets.
To prevent future attacks, it is recommended that GitHub Actions be pinned with hashes instead of version tags. ADevelopers can also use GitHub’s allow-list feature to permit only approved actions.
Tip! Phishing campaign attacks 12,000 GitHub users with rogue OAuth app