Cyber criminals are abusing the Azure-based Microsoft Trusted Signing platform to provide malware with certificates. Microsoft indicates that it is actively monitoring for possible abuse of the service.
It is very useful for cyber criminals to provide their malicious code with an official certificate, in this case for three days. This way, the code can be disguised. In addition, this code can easily pass security filters. Normally, these filters block unsigned exe files, for example.
It is even better for cyber criminals if the malware uses Extended Validation (EV) code-signing certificates. These special certificates ensure that the code is automatically trusted by many security tools. This is due to the rigid certification process that is normally required for SmartScreen.
The EV certificates are difficult to obtain. But cyber attackers can still get their hands on them by stealing them from other companies or through a fake company. Also, if an EV certificate is discovered to have been misused, it is immediately revoked and can no longer be used, so the criminals have to be careful.
Misuse of Microsoft Trusted Signing service
Recent research by various security specialists, such as that of MalwrHunterTeam, shows that cyber criminals have found an easier way to officially register malicious code.
The Azure-based Microsoft Trusted Signing service offers short-term three-day certificates for code that are officially signed by Microsoft. The service also offers additional security features and the certificates also give the same reputation boost for SmartScreen as those for exe files.
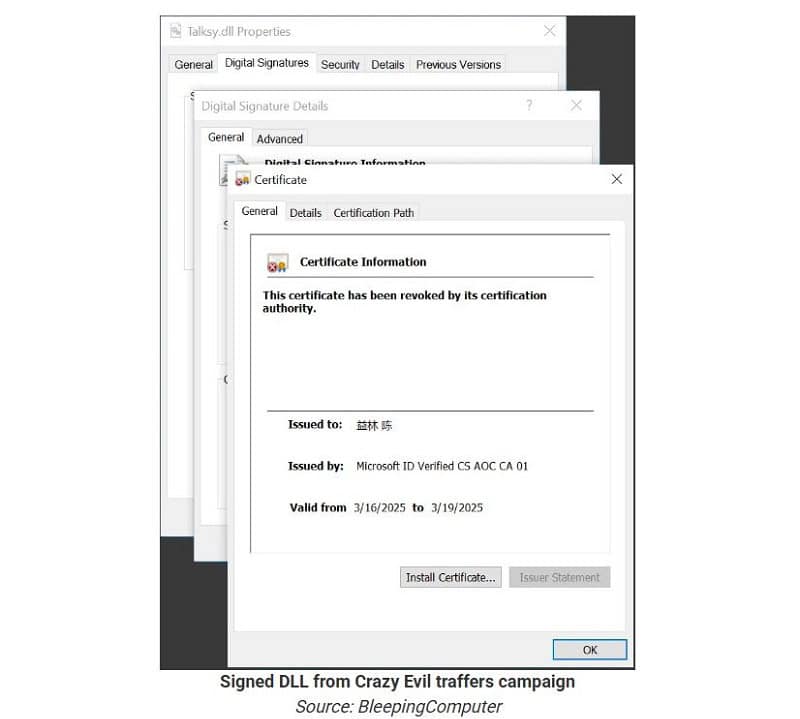
Specifically, Microsoft Trusted Signing-signed ‘Microsoft ID Verified CS EOC CA 01’ certificates are now in circulation. When this certificate expires after three days, signed exe files are still considered valid until the user revokes them.
The misused certificates have since been found in current malware campaigns, including a Crazy Evil Traffers campaign to steal cryptocurrency and in the Lumma Stealer campaigns.
Easier option than EV certificates
Researchers indicate that the abuse of the Microsoft service is mainly due to convenience. For a long time, EV certificates were standard, but Microsoft has announced changes to this. This was mainly because these certificates were not clear to everyone, from users and publishers to cyber criminals.
A simpler certificate, such as via the Microsoft Trusting Signing service, is therefore also more convenient, even for cybercriminals. This is because the verification process is simpler.
Companies are only issued a certificate through the Microsoft service if they have been active for at least three years, but individuals can register and are approved more easily. This is for when they agree that the certificates are issued under their own name. Cybercriminals naturally have easier options for this.
Microsoft response
In a response to BleepingComputer, Microsoft indicates that it uses threat intelligence to monitor the certificate issuing process. This technology helps to detect misuse and abuse of certificates and to revoke them immediately. The abused accounts are also suspended.
The tech giant has now taken action against the malware samples that the security researchers and BleepingComputer forwarded.
Also read: Phishing campaign attacks 12,000 GitHub users with rogue OAuth app