The new Crocodilus malware for Android focuses on emptying users’ smartphone crypto wallets using extensive social engineering tactics.
Security researchers at ThreatFabric recently discovered the Crocodilus malware variant for Android. They believe this mobile OS malware is a good example of modern banking malware. It displays all the characteristic features, such as overlay attacks, keylogging, remote access attacks, and ‘hidden’ possibilities for remote control.
This makes it possible to control a device, monitor it, and harvest data from it. The malware aims to steal the contents of crypto-wallets stored on the smartphones in question, including the seed phases of these apps.
Attack plan
The hackers try to gain access to victims’ Android devices by installing a dropper that bypasses all protection options of Android 13 and later.
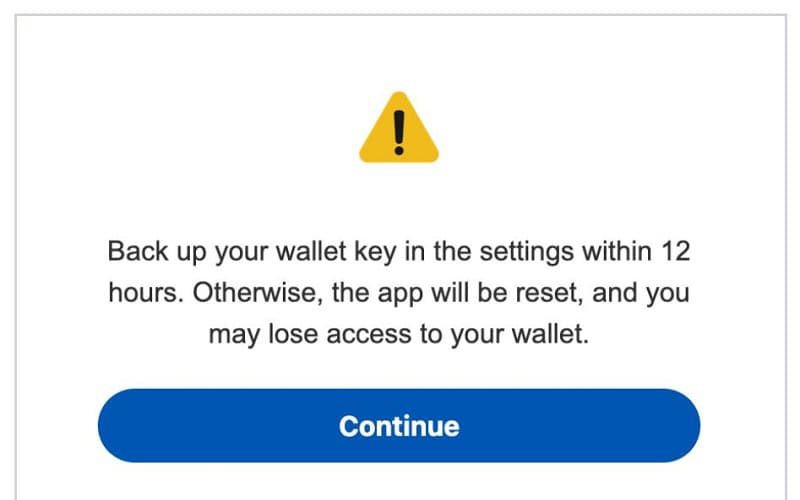
Via a social engineering prompt, victims are asked to update their wallet key within 12 hours; otherwise, they will lose access to their wallet. When victims navigate to their seed phase or the wallet key, the Crocodilus malware can steal the text using an Accessibility Logger.
If the malware gains access to Android’s Accessibility Service, which is normally intended to help people with disabilities, and gains access to screen information, it can perform navigation movements and monitor app launches.
When victims open their banking or crypto app, Crocodilus loads a fake overlay over the real app to steal users’ login credentials.
In total, the Crocodilus malware can execute 23 commands on a hacked Android device, including call forwarding, launching specific apps, sending push notifications, receiving text messages and sending them to contacts, and more.
The malware also has RAT functionality, allowing the hackers to perform actions on the screen themselves and take screenshots of the Google Authenticator app for later use.
Turkish origin
The ThreatFabric researchers state that the Crocodilus malware is primarily spread by convincing victims to install droppers via malicious websites, fake advertisements, social media or text messages and Android app stores other than Google Play.
Based on the bank accounts affected, the hackers are particularly active in Turkey and Spain. The malware is thought to be of Turkish origin. Security experts expect the hackers to expand their activities to other countries soon and to target apps other than crypto wallets and banking apps.
Android users are warned not to download APKs from outside Google Play and to ensure that Play Protect is always enabled on their device.
Also read: Google to help developers make Play Store more secure