
MITRE CVE database saved after last minute reversal
The US government is extending funding for the Common Vulnerabilities and Exposures (CVE) database by eleven ...

The US government is extending funding for the Common Vulnerabilities and Exposures (CVE) database by eleven ...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.

Security researcher Paulos Yibelo revealed about ten bugs that made it very easy to steal sensitive informatio...

According to Gemalto research, only 48 percent of organisations can detect an infringement of Internet or Thin...

Researchers from Crowdstrike, FireEye and McAfee Labs argue that the ransomware called Ryuk is made in Russia....
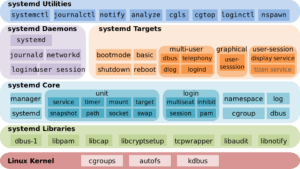
Systemd doesn't make any friends. The widely used but little-loved system and service manager in most Linux di...

Cisco Email Security Appliances with AsyncOS are vulnerable to a devastating attack for which a hacker only ne...

Hackers often use legitimate websites like GitHub and Dropbox to spread cryptographic currency denial malware....

According to the 2018 Application Protect Report of F5 Labs, a large number of companies worldwide are struggl...

A new hack campaign has been discovered that uses various techniques to manipulate the DNS records of several ...

Mimecast informs Techzine that it has found a serious memory leak in Microsoft Office, which may leak sensitiv...

A security researcher has published a tool that can bypass various two-step verifications commonly used on pla...