Cisco launches Foundation AI and introduces open-source security AI model
Cisco is launching a new initiative today at the RSAC 2025 Conference: Foundation AI. This new team within Ci...

Cisco is launching a new initiative today at the RSAC 2025 Conference: Foundation AI. This new team within Ci...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.

LockBit has been claiming a hefty share of ransomware damage for years. Now the criminal organization is in d...

Wiz is acquiring cloud security company Gem Security. Although the amount was not disclosed, the acquisition ...

Google recently introduced an enterprise-targeted paid version of its Chrome browser: Chrome Enterprise Premi...

A security systems app appears to have leaked highly sensitive data. MASmobile Classic, intended for alarm sy...

A critical vulnerability has been identified in the programming language Rust, potentially allowing attackers...

The Linux data compression tool xz-Utils is available again through GitHub. Last month, a backdoor was discov...

Microsoft has fixed a number of already exploited vulnerabilities in its monthly Patch Tuesday update. The mo...

The new platform is designed to visualize and investigate security incidents in cloud, email, network, endpoi...

Purple AI, the new generative AI addition to the SentinelOne platform is going to save a lot of time for secu...
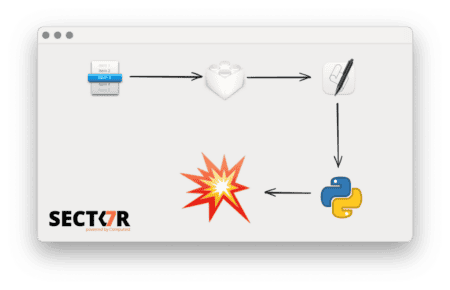
The process injection vulnerability allows access to webcams, microphones and sensitive information. Thijs...